Modernize your security and backup with integrated cyber protection with Security + XDR

All-in-one cyber protection
The Braintree Group integrates backup, recovery, and next-generation, AI-based anti-malware and protection management into one solution. This integration and automation provide complete cyber protection while increasing productivity and decreasing TCO.
With one agent, one web-based management console, and one license, you can remove the complexity and risks associated with non-integrated solutions while benefitting from the five critical stages of cyber protection - prevention, detection, response, recovery, and forensics.

All-in-one
Prevent client downtime and data loss with essential cyber protection
Cyber Protect Cloud unites backup and next-generation, AI-based anti-malware, antivirus, and endpoint protection management in one solution. Integration and automation provide unmatched ease for service providers — reducing complexity while increasing productivity and decreasing operating costs.
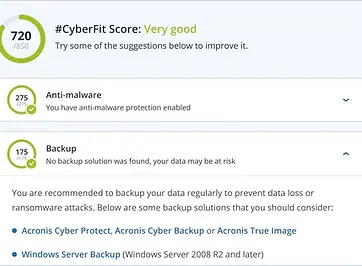
The world’s best backup and recovery
Full-image and file-level backup and recovery to safeguard workloads on more than 20 platforms – with near-zero RPOs and RTOs
Enhanced with essential cyber protection at no cost
Аdvanced AI-based behavioral detection engine stops malware, ransomware, and zero-day attacks on client workloads.
With protection management
Integrates data protection, cybersecurity, and endpoint management into a single solution with centralized management. Seamless integration with RMM and PSA systems.
Stages of modern cyber protection
To deliver thorough protection for our customers, Our vision and products are based on a multi-stage process rather than simply detecting and blocking threats, leaving other risks uncovered.
Prevention
Don’t wait for threats to hit, proactively protect your clients and limit their attack surface.
Recovery
Restore client data quickly and safely so no data is lost, with near-instant availability, in case of compromise
Detention
Detect issues and threats in real-time before they pose risk to the IT environment.
Forensics
Mitigate future risks and enable easy investigations by collecting forensics information.
Response
Enable quick actions that immediately mitigate the risk.